
Getty Images
Researchers have developed an inexpensive smartphone attack that cracks the authentication fingerprint used to unlock the screen and perform other sensitive actions on a variety of Android devices within 45 minutes. .
Called BrutePrint by its creators, the attack requires an adversary to have physical control of a device if it is lost, stolen, temporarily surrendered, or unattended, for example, while the owner is asleep. The goal: to gain the ability to perform a brute-force attack that will try multiple fingerprint guesses until one is found to unlock the device. The attack exploits the device’s SFA (smartphone fingerprint authentication) vulnerabilities and vulnerabilities.
Overview of BrutePrint
BrutePrint is a cheap vulnerability exploit attack that allows people to unlock devices by exploiting various weaknesses and vulnerabilities in smartphone fingerprint authentication systems. Here is the workflow of these systems, which are usually abbreviated as SFAs.
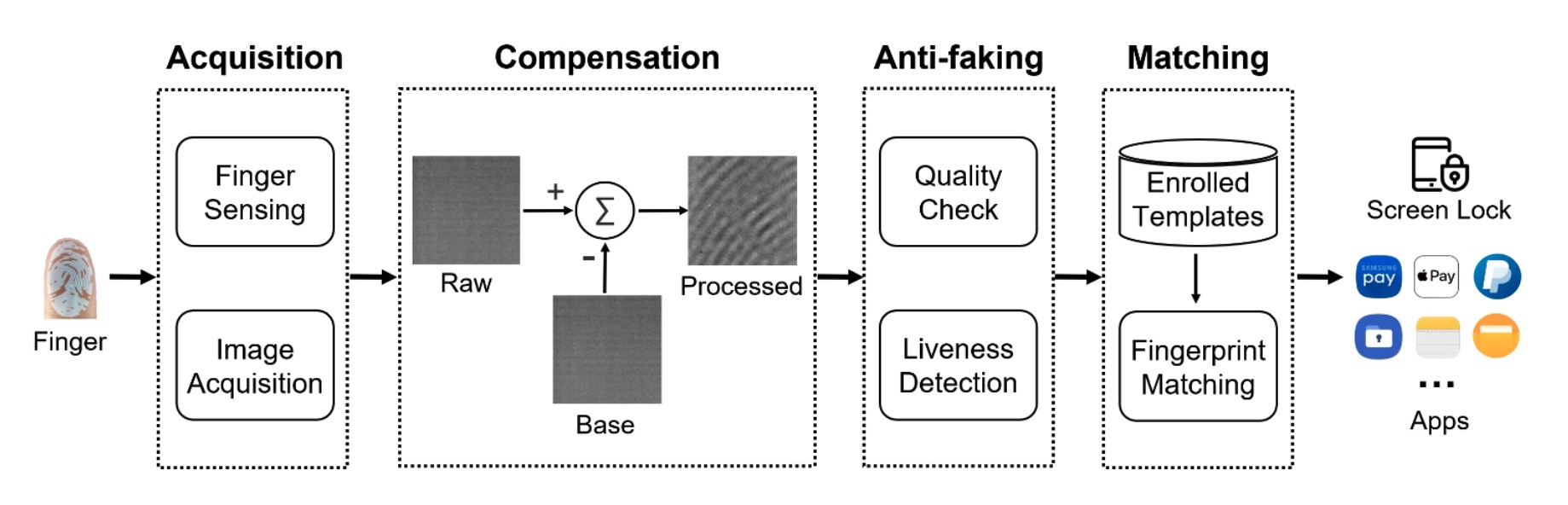
The workflow of a smartphone fingerprint authentication system.
The core of the equipment required for BrutePrint is a $15 circuit board containing (1) an STM32F412 microcontroller from STMicroelectronics, (2) a bidirectional, dual-channel, analog switch known as RS2117, (3) an SD flash card with 8GB of memory, and (4) a board-to-board connector that connects the phone’s motherboard to the fingerprint flexible printed circuit of the fingerprint sensor.
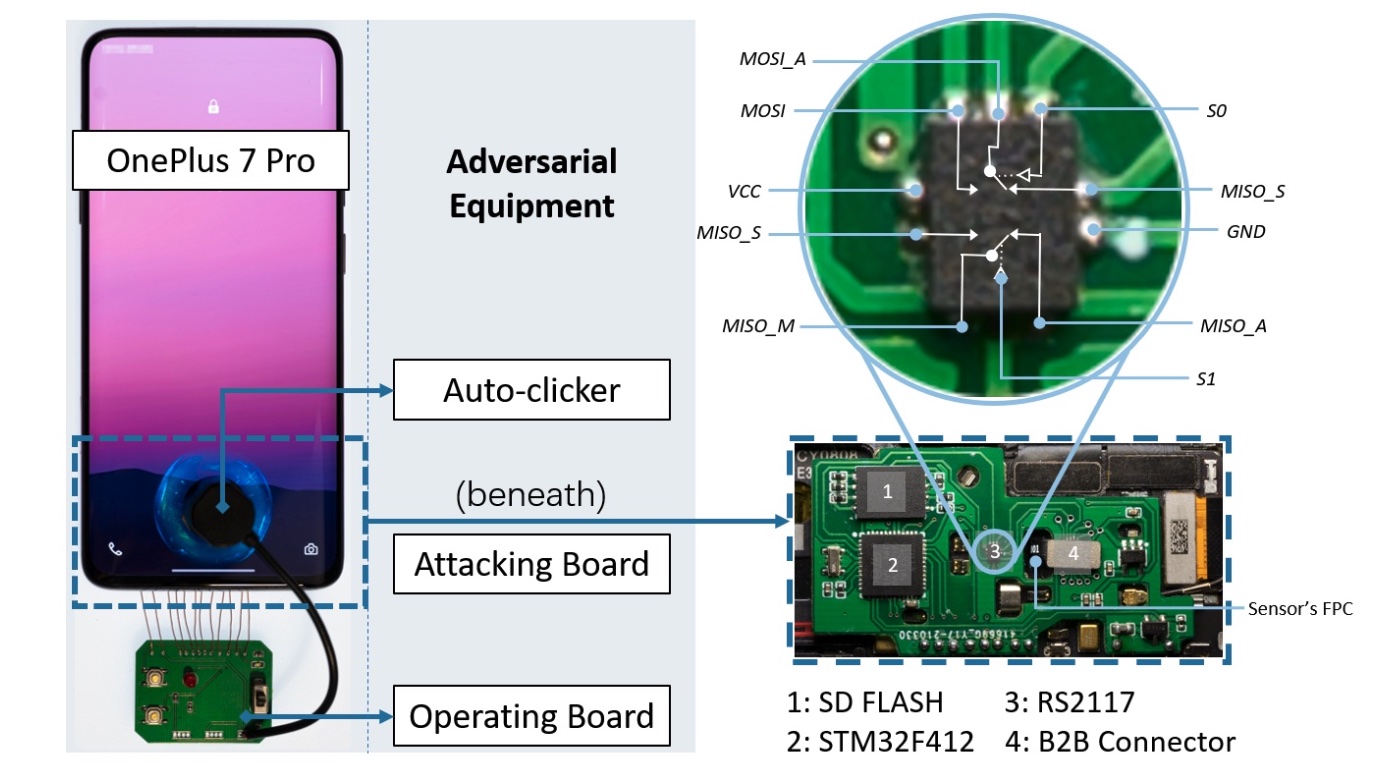
The adversary device that forms the core of the BrutePrint attack.
Additionally, the attack requires a database of fingerprints, similar to those used in research or leaked in real-world breaches like this one.
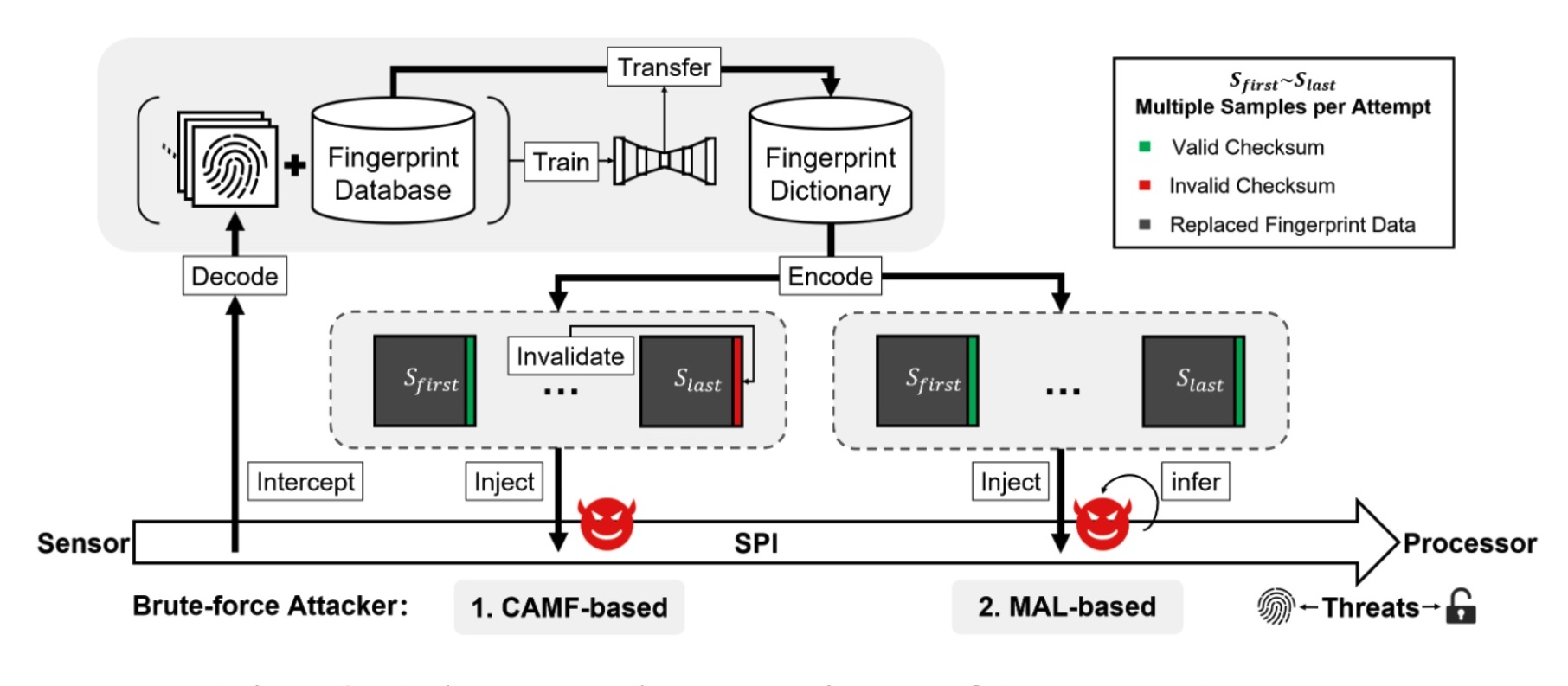
An overview of the BrutePrint attack.
Not all smartphones are created equal
More on how BrutePrint works later. First, a breakdown of how the different phone models work. In total, the researchers tested 10 models: Xiaomi Mi 11 Ultra, Vivo X60 Pro, OnePlus 7 Pro, OPPO Reno Ace, Samsung Galaxy S10+, OnePlus 5T, Huawei Mate30 Pro 5G, Huawei P40, Apple iPhone SE , Apple iPhone 7.
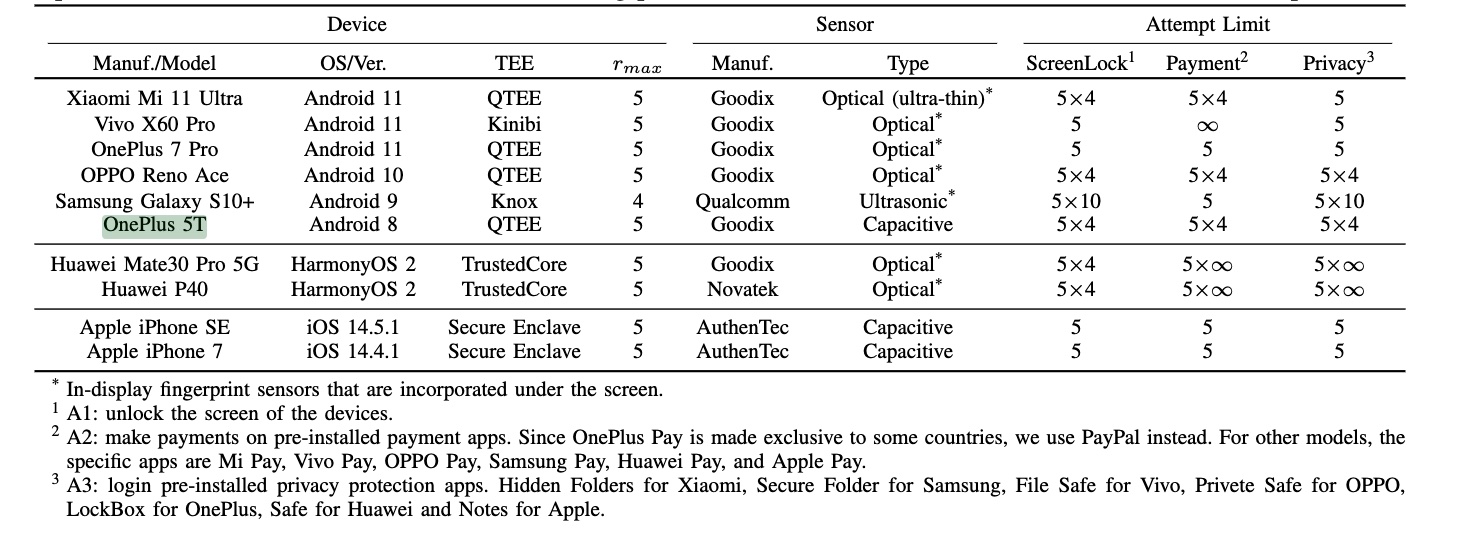
A list of devices tested along with the various characteristics of the devices.
Researchers test each for different vulnerabilities, weaknesses, or susceptibility to different attack methods. The evaluated attributes include the number of samples in multi-sampling, the availability of error-cancel, support for hot-plugging, if the data can be decoded, and the data transmission frequency of SPI. In addition, the researchers tested three attacks: attempt to bypass the limit, hijack the fingerprint images, and force the fingerprint.
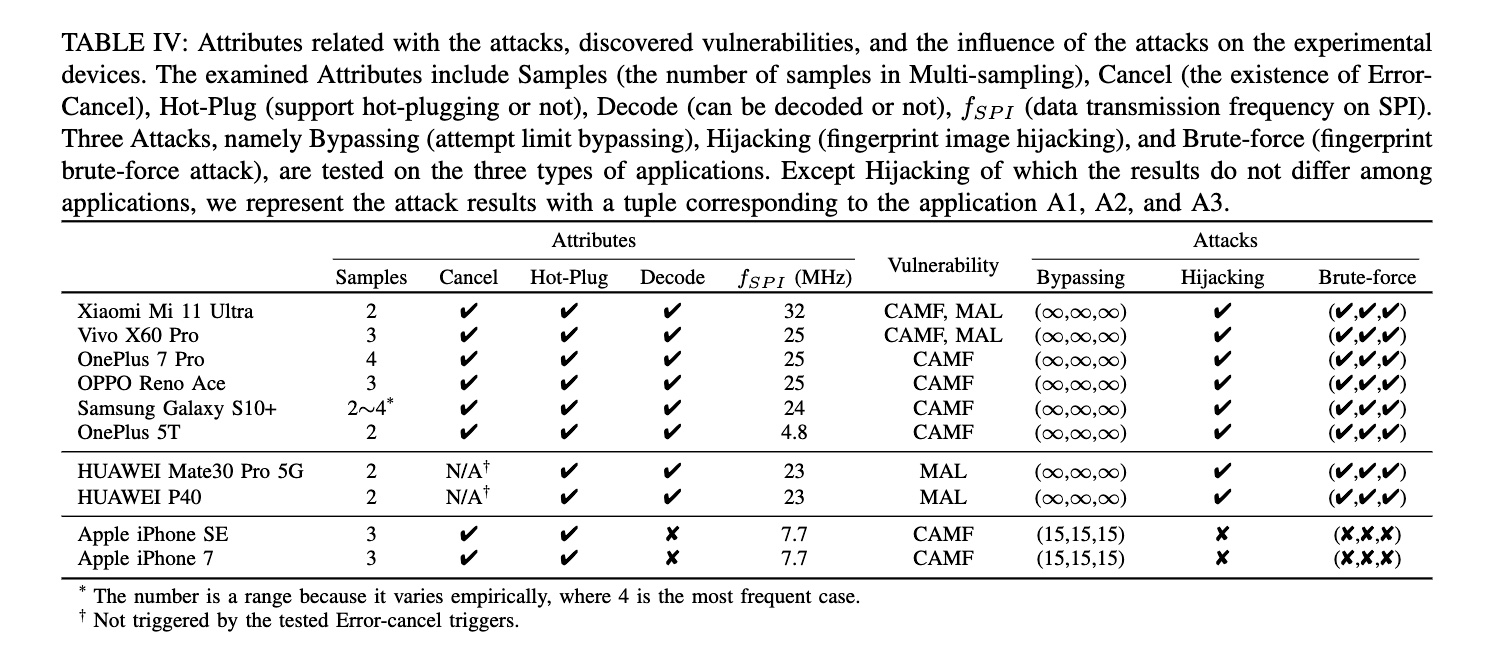
Results of different attacks on different devices tested.
Finally, the researchers provided results showing the time required for different phones to force their fingerprints. Since the amount of time depends on the number of prints allowed, the researchers put each one in a print.
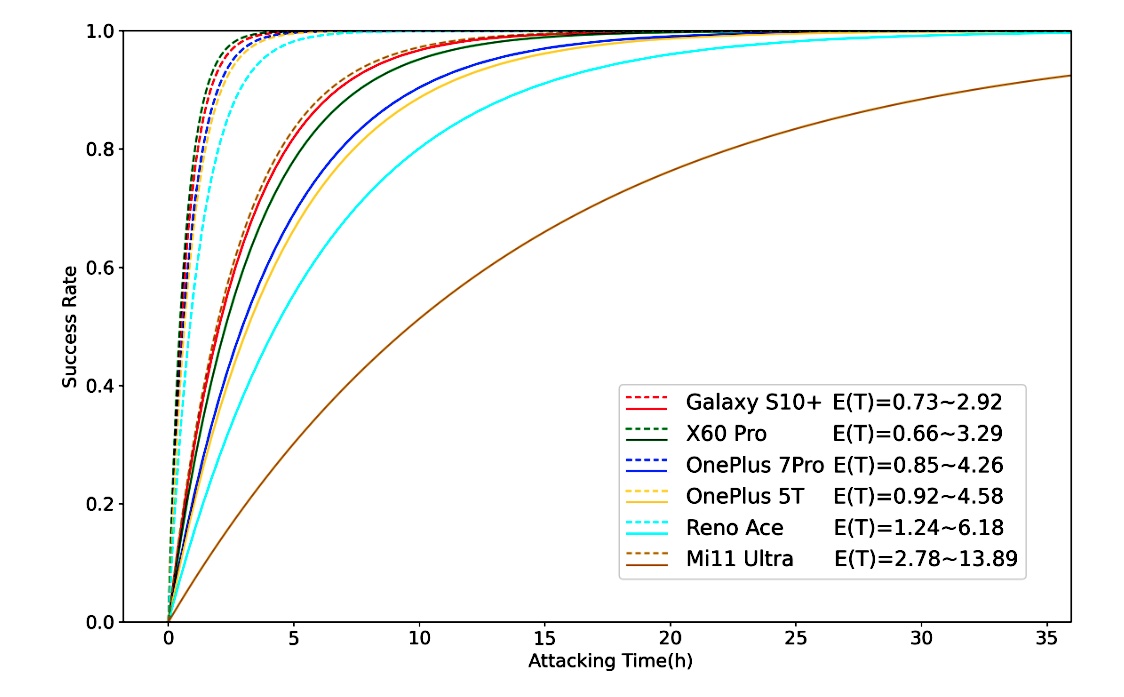
The success rate of different devices was tested, with the Galaxy S10 + taking the least time (0.73 to 2.9 hours) and the Mi11 the longest (2.78 to 13.89 hours).
Although the specifications are different, the result is that BrutePrint can test an unlimited number of fingerprints for authentication on all eight of the Android models tested. Depending on a variety of factors, including the fingerprint authentication framework of a specific phone and the number of fingerprints stored for authentication, this takes anywhere from about 40 minutes to 14 hours.
